Introduction
Antivirus software is designed to protect computers from malicious software (malware) at the static, dynamic, and network levels. Antivirus software is commonly installed on endpoints and servers; thus, network security is differentiated between IPS and firewalls.
In the modern digital age, antivirus software are the first line of defense against various digital threats. These programs are designed to protect our endpoints from viruses, malware, and other threats that can harm our sensitive information and cause significant damage. However, despite their great importance, there are situations in which the antivirus identifies a file or process as malicious when in fact it is completely safe. This false detection, known as a False Positive, can cause many problems for both private users and organizations.
To understand that, we can check that CCleaner is a popular tool for cleaning and improving computer performance developed by the Piriform company. The software is useful for cleaning temporary files, fixing registry errors, and managing programs that start when the endpoint is turned on. However, the nature of the actions performed may often be flagged as malicious by various anti-virus software.
Below is a breakdown of the factors:
· Registry Repair: The software removes unused or unnecessary registry keys, which aim to improve computer performance and reduce system loading time.
· Management of startup programs: CCleaner allows users to manage the list of programs that start automatically when the operating system boots, which can improve the computer’s boot time.
· Software removal: The software provides a tool to remove software installed on the computer more thoroughly than the built-in Windows software manager.
This kind of operation, often antivirus software, is flagged this kind of behavior as malicious, which can cause false positives and interrupt the user’s experience.
Definition and Explanation
A false positive in the context of antivirus software occurs when the program mistakenly identifies a safe file or process as malicious. This erroneous detection can result from overly aggressive heuristics, outdated or incorrect signature databases, or the complex behavior of legitimate applications that mimic the characteristics of malware. False positives can disrupt normal operations by blocking essential software, prompting unnecessary alerts, and causing users to question the reliability of their security tools. While antivirus programs aim to protect systems from genuine threats, the challenge lies in balancing vigilant detection with minimizing these false alarms.
Common Examples of False Positives:
- Legitimate software mistakenly flagged as malware
- System files or updates identified as threats
- Custom or rare tools and scripts marked as suspicious or malicious
- Incorrect detection of harmless activities as suspicious
Comparing actions between legitimate software and ransomware malware

False Positive Example
For example, we used nssm.exe, an executable file associated with NSSM, the Non-Sucking Service Manager. NSSM is a service helper program for Windows that is designed to help you run any executable as a Windows service.
Executable Details:
File Name: nssm.exe
Size: 288.00 KB
File Type: Executable
Architecture: PE32+
MD5: d9ec6f3a3b2ac7cd5eef07bd86e3efbc
SHA-256: 472232ca821b5c2ef562ab07f53638bc2cc82eae84cea13fbe674d6022b6481c
Using the exeinfo PE tool, we detected that the file was developed in C++ and is not packed. Typically, malware is packed for evading from detection and analysis. Typically, antivirus software detects obfuscated strings to identify packing techniques that threat actors commonly used for defense evasion techniques.

After uploading the file to the VT (VirusTotal) platform, we can notice that 4 different kind antivirus software detected the program as malicious. We observed that the file could be identified as malicious based on its hash or signatures.

To understand the reason why the antivirus software detected the file as malicious, we need to dive deeper into the file’s characteristics.
Static Analysis
In this section, we will analyze the file without executing it. We will examine what causes the file to be detected by the antivirus statically. Antivirus software scans our files before we execute them, so let’s understand how this False positive can happen.

In the PEstudio tool, we can notice the usage of important Windows DLLs. The KERNEL32 and ADVAPI32 libraries contain functions that are frequently used by both legitimate and malicious software.

Antivirus software can include the analysis of strings to evaluate a file’s maliciousness. After checking the file’s strings with Floss, some artifacts might mistakenly cause an antivirus program to identify the file as malicious.
The presence of certain strings commonly found in malware can trigger a static detection.
In the screenshots below, we can notice the usage of Windows API functions. Because of the combination of the usage, Antivirus software can detect and flag these kinds of strings as malicious.



The file contains many references to Windows API functions such as CreateFileW, DeleteService, RegSetValueExW, LoadLibraryW, and others. Malware often uses these functions to manipulate system resources.
CreateFileW:
Opens or creates a file, pipe, or other input/output device and returns a handle to the created or opened object. Commonly used by both legitimate and malicious software to access and manipulate files.
DeleteService:
Deletes a service from the system after it has stopped. This action removes the service and all its related settings from the registry. Service management processes and malware are commonly used to remove important services or create a sense of harm.
RegSetValueExW:
Sets or modifies a value in the Windows registry. Allows the software to write data in the registry, which is done by legitimate software to manage system settings and by malware to change system settings maliciously.
LoadLibraryW:
Loads a dynamic link library (DLL) into memory and returns an identifier for the library. Using this process allows programs to extend their functionality by loading external code, which is also done by malware for loading malicious code.
Malware frequently controls system processes by using functions related to process and thread management (CreateProcess, CreateThread, TerminateProcess, etc.).
During the static analysis of the nssm.exe file, we detected the use of important Windows DLLs that contain functions frequently used by both legitimate and malicious software. This can cause antivirus software to detect the file as malicious, even if it is legit.
Dynamic Analysis
Now, let’s proceed to dynamic analysis, where we will observe the file’s behavior during execution. This step is crucial for understanding its actions and determining why the file is detected as malicious.
First, we ran the file on Sandbox to check what the program does
When we ran the file, a dialog box showed the NSSM (Nonsense Service Manager) commands and features. The dialog box includes information about installing, editing, removing, and managing a system of services.

The displayed commands and accompanying information indicate that the nssm.exe file functions as a legitimate system service management rule. but it also connects to what we found in the strings and library of the file.
Analysis Code
For analyzing the file, we used IDA, which can decompile it into code. IDA allows us to thoroughly examine the file’s internal structure and logic, providing deeper insights into its behavior and potential malicious activities. Through this process, we can identify specific functions, API calls, and code patterns that contribute to the file being flagged as malicious by antivirus software.
By the code, the file uses the DeleteService function to delete services from the computer. deleted service can appear as malicious action for anti-virus
Error checking and generating error messages: The code checks the result of the DeleteService function call. If the function fails (that is, the value of eax is not zero), the code generates an error message with a specific message ID and calls additional actions to handle the message.
Creating an error message and calling for further actions: including and returns an error, the code creates an error message by pushing a particular message ID onto the stack, calling operations that return a value, and using the adjusted value as a parameter to another function to handle the message.
ClosingServiceHandle: After handling the error or if there was no error, the code closes the service by calling the CloseServiceHandle function.

The code uses the RegSetValueExW function to write a value in the Windows registry.

The code checks the value returned by the RegSetValueExW function. If the function failed (that is, the value of eax is not zero), the code calls the GetLastError function to get the last error code and continues with the error message.
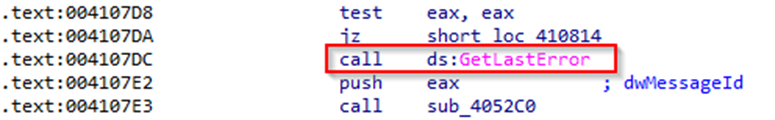
if there is an error, the code pushes the error code and additional information onto the stack, calls the function that returns a value, and uses the adjusted value as a parameter to the function to handle the error message.

After performing the actions or handling the error, the code closes the registry key by calling the RegCloseKey session.
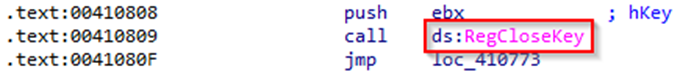
The code performs several actions aimed at writing values in the Windows registry, checking the results of calls to functions, asking for necessary errors, and closing registry keys. These actions include:
Writing values in the registry: Using the RegSetValueExW function to values in the registry, which may appear malicious if the critical values are changed.
Error checking and treatments: checking the results of the call to the function and recording error messages in case of failure.
Closing registry keys: Closing registry keys in an orderly manner using RegCloseKey.
This article discusses how antivirus programs can mistakenly identify legitimate software as malicious, leading to false positives. The code analysis performed using IDA reveals that certain legitimate operations within the software can trigger these detections.
How to avoid false positives in the future
· Anti-Virus based on AI
The use of AI in antivirus systems offers more advanced and effective solutions for detecting malware and preventing false positives. Machine algorithms, which are part of the subfield of AI, can learn the patterns and behaviors of files and malware based on vast amounts of data. These models can more accurately distinguish between legitimate behavior and malicious execution by analyzing the complexity of various characteristics, such as binary code, network behavior, and operations on a system.
· Using a sandbox platform (such as Hybrid-Analysis) to analyze the file process and ensure its integrity
Using a sandbox platform like HybridAnalysis to analyze the file allows you to identify and verify the integrity of the file efficiently and accurately. The Sandbox platform runs the file in an isolated and secure environment, where you can track every action the file makes to the operating system. On analysis, the platform checks for idle behaviors such as unauthorized access to files, registry changes, and unusual network traffic. HybridAnalysis, for example, provides optional reports on file operations and allows users to gain deep insights into file behavior.
Summary
In the modern and developing era, we are exposed to many software and scripts designed to make our daily work easier and improve our efficiency. However, there are cases where we encounter a misidentification of the antivirus programs, identifying legitimate programs as malicious. This detection, known as False Positive, can be a problem and impair our normal operation.
However, it is important to remember that the main purpose of antivirus software is to keep our computers safe from viruses and malware. Therefore, we must be vigilant and carefully check the software we use, to make sure that they are indeed legal and safe. By using advanced tools such as artificial intelligence, sandbox platforms and more, You can reduce the number of false positives and maintain the right balance between protecting the system and maintaining normal and efficient activity.


+ There are no comments
Add yours